Protect your business from embarrassing security failures with Corsaire’s flagship penetration testing and information security consultancy services.
Standard: PCI Data Security Standard (PCI DSS) Version: 1.0 Date: March 2015 Author: Penetration Test Guidance Special Interest Group PCI Security Standards Council


Award Winning Cyber Security Providers in Technology and Consulting Services including Penetration Testing – Cyber Security Company of The Year 2016.
Oct 13, 2013 · For the second post in the cyber series for business owners, I’d like to focus upon penetration testing. Again, credit goes to infosec engineer Shaggie Scheferman for his technical input. I’d like to first establish what a penetration test is (and what it is not), look at some of the reasons why

Penetration testing (also known as intrusion detection and red teaming) is security-oriented probing of a computer system or network to seek out vulnerabilities that an attacker could exploit. vulnerabilities that an attacker could exploit.
Enterprise network penetration test results data can be confusing. Learn how to conduct analysis after network pen testing to make the most of the data.
Penetration Test Report MegaCorp One August 10th, 2013 Offensive Security Services, LLC 19706 One Norman Blvd. Suite B #253 Cornelius, NC 28031 United States of …
The cone penetration test (CPT) is a common in situ testing method used to determine the geotechnical engineering properties of soils and assessing subsurface stratigraphy.



Selecting the right penetration test tool can be a hassle. To make your life easier, we have put together a list of proven penetration testing tools.
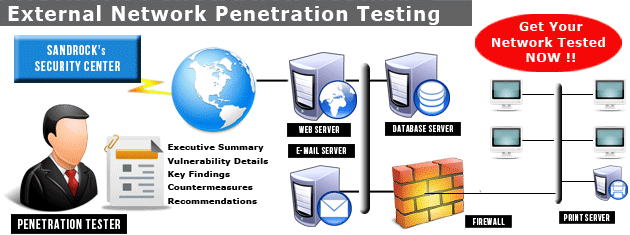
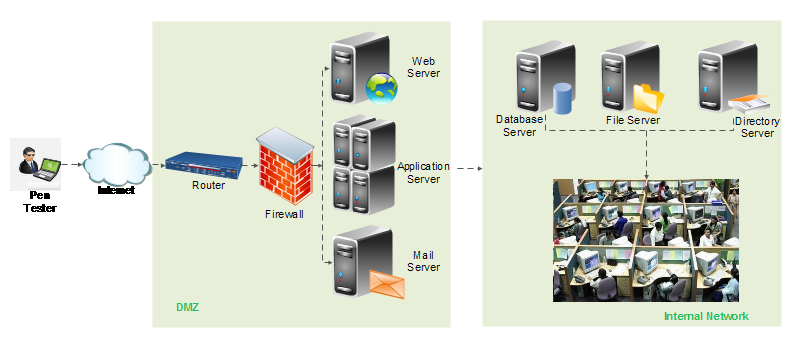
External Penetration Test . An External Penetration Test differs from a vulnerability assessment in that it actually exploits the vulnerabilities to determine what information is actually exposed to the outside world. An External Penetration Test mimics the actions of an actual attacker exploiting weakne
